
This article will explore the path to developing secure devices by introducing 13 best practices for Internet of Things (IoT) security and how to implement them in iot applications to ensure regulatory compliance. The 13 best practices include no default passwords, security update mechanisms, and an end-of-life policy that clearly informs customers. While global legislation is still evolving, we all know it will contain steps similar to these 13 best practices. Once these measures are implemented, they could, in theory, easily be adapted to any other requirements that European EN 303 645 and the evolving US iot Security Improvement Act (NISTIR 8259) may impose.
Iot security
Security is essential to enable devices to work together in a trusted network, share personal data within the network, and enable private operations through cloud services. Similarly, a secure foundation is needed to manage updates and purchases.
Iot device vendors realize that the value of their IP(intellectual property) is equal to the value of their business. The possibility of IP theft is very high. In fact, according to the latest Intellectual Property Protection and Enforcement report, the European Union estimates that up to $60 billion in IP may be stolen each year. In addition to the economic consequences, such IP theft could have a potential impact on around 300,000 jobs in the EU alone.
Consumer protection is driving standards and safety legislation around the world. For example, consumer electronics shipped to Europe must comply with the European standard EN 303 645. In addition, iot devices are subject to the privacy regulations outlined in the GDPR regulations. This includes a clear obligation to protect users' personal data and to ensure that such data can be deleted during the life of the product or when the product is sold or transferred. Similarly, all data provided as part of a service, even a simple coffee machine voice command, falls under the purview of the regulation.
The GDPR sets out clear penalties for violations, with a minimum fine of €20 million, or 4% of a company's total sales, if a company is found to have deliberately broken the law.
Consumer regulations
With the introduction of EN 303 645 and the US iot Security Improvement Act (NISTIR 8259), the consumer iot market is under increasing pressure to comply with security standards. However, this is not limited to iot consumers, regulations are also rapidly evolving in other markets, such as the requirements of IEC 62443 for the Industrial Internet of Things (Industry 4.0) and similar requirements for the medical and automotive industries.
EN 303 645 is very similar to the U.S. iot Security Improvement Act, and its roots can be traced back to the work of the iot Security Foundation.
The iot Security Foundation is a successful industry forum that grew out of the need to identify existing "best practices" or security practice guidelines and how they can be applied to emerging iot challenges.
The goal of the Consumer iot Security Practice Code is to provide guidance on how to adopt a secure design approach during the development, production, and maintenance of iot products throughout their life cycle. These practices bring together accepted iot security best practices.
Consumer iot Code of Practice
Guidelines and practices cover everything from secure device startup, encrypted device identity, roots of trust, operating systems, credential management, and encryption to security software and software update policies.
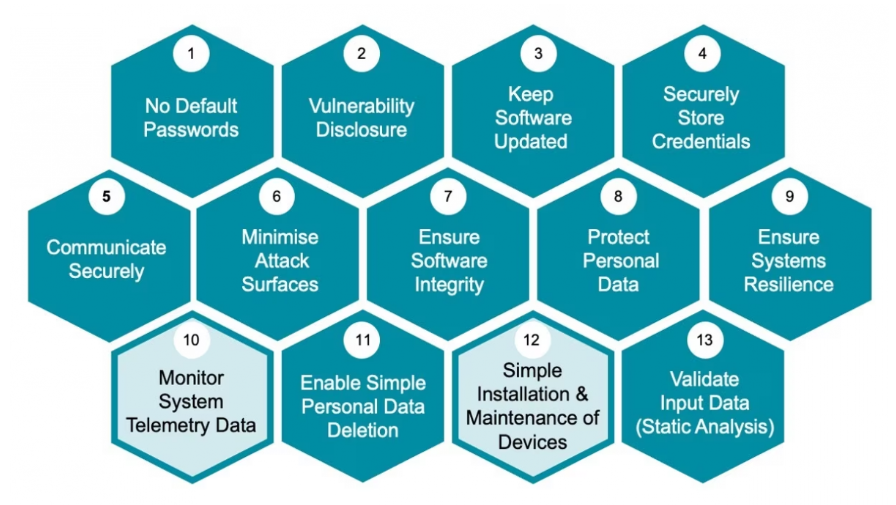
The EN 303 645 standard focuses on 13 best practice requirements, including three core elements: no default passwords, vulnerability disclosure and keeping software up to date.
Let's explore these best security practices that can be directly applied to iot applications:
1. There is no default password
Sounds obvious, but more needs to be done to make it happen. Ideally, the default password should be derived from or injected into the device itself. A sensible idea is to use a variety of algorithms based on device-specific hashes to generate passwords in cases where the sequence number does not have enough entropy and the device uses a hash-based algorithm such as SHA-256.
2. Implement vulnerability disclosure policy
In a nutshell, it's about the company's disclosure policy, having a dedicated director in addition to customer contact activities and vulnerability communication.
3. Keep your software updated
As the number of iot devices used in businesses continues to increase, keeping them updated will be a challenge. Teams that develop a strategy early in deployment will find themselves easier to manage than teams that don't have a strategy for iot software updates. Updates must be timely and should not affect the operation of the device. Update policies need to enforce anti-rollback mechanisms so that older versions don't become possible attack vectors.
The software update practice also includes an end of life policy to provide and push updates to devices within a specified period.
4. Securely store credentials and security-sensitive data
This practice suggests that any credentials should be securely stored within the service and on the device. Hard-coded credentials such as passwords and bank account information are not acceptable in device software. The MCU's device-specific security features and memory management should always be fully enabled to protect security-sensitive data.
5. Communication security
IoT devices should communicate securely using the Secure Transport Layer Protocol (TLS) or Lightweight Encryption (LWC) and always use the latest version. This means that security-sensitive data should be encrypted during transmission and that keys should be managed securely.
6. Minimize the attack surface
The goal is to minimize the exposed attack surface, meaning that all devices and services should operate according to the "principle of least privilege." This is one of the most important principles related to code quality, as software flaws or code vulnerabilities are the gateway for hackers to exploit iot devices for attacks.
Code quality needs to be enhanced by design. There are many standards available, but one in particular is the CERT C coding standard, developed and owned by Carnegie Mellon University's School of Software Engineering, which provides secure coding rules for the C programming language. The goal of these rules and recommendations is to develop a secure, reliable, and stable system, such as eliminating undefined behavior that can lead to undefined program behavior and exploitable vulnerabilities.
Most common security vulnerabilities are known, yet developers keep injecting the same bugs over and over again. The good news is that these bad coding habits are covered in coding standards such as mitre.org's Common Weaknesses Enumeration (CWE), and point out other areas of concern, such as data injection, null pointer vulnerabilities, and string parsing errors. MISRA C and MISRA C++ also promote safe and reliable coding practices to prevent security vulnerabilities in code. High-quality static analysis tools include checks for CWE, MISRA, and CERT C, so you can improve code quality day by day.
7. Ensure software integrity
This means that software on iot devices should be verified using a secure boot mechanism. If unauthorized changes are detected, the device should alert the consumer and ensure that the software is verified and protected.
The secure startup process is critical to ensuring the integrity of iot devices. Security boot is often referred to as trust root. The trust root must be a computing engine that performs a large number of operations and has a set of unconditional trust capabilities. The root of trust is then implemented with a secure boot loader/manager. In this way, user application validation is ensured, which is a key part of every boot cycle.
8. Protection of personal data
This article does not discuss how personal data is managed and protected. This may vary slightly depending on local standards and data protection laws in different regions. Still, this guideline is important, and companies need to be transparent and allow consumers to withdraw their information at any time.
9. Ensure system resilience
Iot devices should be resilient because if a device has vulnerabilities and someone attacks it, you don't necessarily want to just shut it down, especially a device like a pacemaker. That would be terrible! So the idea is to make the device resilient enough that it can still provide a restricted service, or at least tell the user what's going on, and that the device should be able to return to the network in an orderly manner in a reasonable state, rather than a massive reconnection.
10. Monitoring system telemetry data
Telemetry is the collection of measurement or other data at a remote point and its automatic transmission to a receiving device for monitoring. Best security practices state that if all telemetry data is collected, such as all usage and measurement data from iot devices and services, it should be monitored for security anomalies.
11. Enable simple personal data deletion
Ownership of iot devices may change, and in the long run, these devices may be reused or discarded. Product designers must implement this in their applications and configure it so that personal data can be easily deleted. Therefore, you can also transfer ownership. Maybe you want to give it to a friend, but you want to delete your data before you give it to them.
12, equipment installation and maintenance is simple
The user interface for iot devices and support services should be intuitive, user-friendly, and provide appropriate feedback for the user actions that affect such policies and their execution.
Manufacturers are advised to test the security of each device with a range of possible configurations, rather than simply using the default configuration. The device's interface should prevent, or at least actively discourage, users from configuring the device in a way that reduces the security of the device.
13. Verify the input data
A final best security practice is to validate input data. This principle refers to not trusting received data and always verifying all interconnections. Before trust is established, devices connected to the network are discovered, identified, and verified, and their integrity is maintained for trusted solutions and services. This may include checking data type, length, format, range, authenticity, origin, and frequency, as attackers use automated tools to exploit potential vulnerabilities such as out-of-bounds access, computation errors, and memory inconsistencies due to not validating data. Hackers can exploit these vulnerabilities to run any code they want and take over control of iot devices.
Code analysis tools for inspecting code are very helpful for testing and validating input data during development, thus protecting applications from bad practices in the field. Automated analysis tools during development and field testing can trigger and point out hidden problems, so source code can be tweaked and iot applications can be prevented from being misused.
Enable security from the start
Following all guidelines and best practices is not easy. Without the right tools, achieving a secure foundation by integrating and combining secure device boot, encrypting device identity, root of trust, credential management, and encryption to secure software and TLS communications and improve code quality can be a lengthy process.
So one of the most recommended solutions is to define security content at the very beginning of the project, when the project starts. This should be a description of the security content necessary to ensure IoT applications are secure and comply with standards and guidelines. Defining security content early allows developers to quickly implement needed security measures, ensuring repeatability and reducing development effort across multiple projects. Secure content can be customized to suit a variety of iot applications.
Security content shall be defined as:
● A strong root of trust ensures device authentication, authorization, and proof, which is the core proof of identity
● Encrypting device identity and ownership structure
● The realization of network security and health depends on the hardware support of equipment
● The Secure Boot Loader/Manager extension supports core boot functionality
● Software updates and other lifecycle management standards
These safety elements provide the basis for a core set of safety features that achieve the design safety required by the guidelines. Once integrated into the development tools, the security content will automatically implement and effectively apply the guidelines, making the process simple and naturally integrated into the development of new iot products.
Conclusion
The Consumer iot Security Standard EN 303 645 is based on 13 best practice guidelines developed by the iot Security Foundation and the UK Government and is widely recognized as the security benchmark for the consumer iot. Both standards and guidelines contain the core requirements that developers should meet for their applications. Businesses must adhere to these core requirements when building iot applications to comply with security regulations.
Heisener Electronic is a famous international One Stop Purchasing Service Provider of Electronic Components. Based on the concept of Customer-orientation and Innovation, a good process control system, professional management team, advanced inventory management technology, we can provide one-stop electronic component supporting services that Heisener is the preferred partner for all the enterprises and research institutions.
